top of page


Deep Learning with Tensorflow.js
Deep learning is a subset of machine learning in artificial intelligence that has networks capable of learning an unsupervised form of...
May 6, 2024


What is Node.js?
Before interpreting the concept of Node.js, it is important to have some fundamental understanding of JavaScript. JavaScript is commonly...
Apr 29, 2024

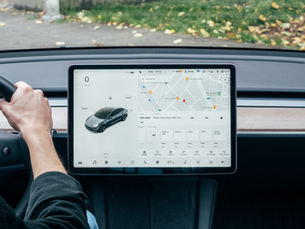
Augmented Reality (AR) in Car Navigation
The pivotal motive of augmented reality technology in navigation systems is to assist the user in providing the useful information and...
Apr 4, 2022


Progressive Web Applications (PWA) - Best Fit for Lite Apps Over Native Apps
As technological developments spread from one part of the world to another, the internet inevitably follows suit. In a world where 66% of the population is carrying a mobile phone, a mobile presence is a must for any individual who seeks success on the internet. In this context, a million-dollar question arises -- how to target mobile and desktop users similarly without building and maintaining a mobile app (for iOS, Android, etc.) and a responsive website at the same time?
Jun 1, 2021


Protecting UI/UX Design Using Intellectual Property
UI/UX design is an essential part of any website and the on-screen controls you used to perform various functions on web apps, make up GUI
May 18, 2021


Open Source Vulnerabilities - What are they and how to check them?
Open-source software offers many benefits to enterprises and development teams, they are subjected to open source vulnerabilities that pose significant risks to application security. Many development teams, be it traditional or agile, incorporate pre-built, reusable open source software components to accelerate the delivery of the product but most open-source software is not subjected to the same level of scrutiny as software that is custom developed. The Open source software
Mar 2, 2021


Reverse Engineering Source Code
Reverse Engineering is a method by which an object is deconstructed for exploring its design, architecture, code and components.
Jan 19, 2021


What is Doctrine of Equivalents?
While there are multiple ways to skin a cat (see discussion on indirect infringement and direct infringement here ), patent infringement can occur in two forms. The first is literal infringement. Literal infringement is when every aspect of the claim is being infringed upon in much the same way the claim was written. The second one, more complex, is an infringement under the doctrine of equivalents. Under this doctrine, the patentee can argue infringement even if each and eve
Sep 2, 2020


Understanding Source Code Quality and Design Quality During Technology M&A
With thousands of transactions and billions of dollars spent on technology mergers and acquisitions (M&A) every year, buyers must protect...
Nov 5, 2019


Source Code Review: Best Practices
"Few tasks excite a defendant less... Engineers and management howl at the notion of providing strangers, and especially a fierce competitor, access to the crown jewels. Counsel struggles to understand even exactly what code exists and exactly how it can be made available for reasonable inspection. All sorts of questions are immediately posed... Put simply, source code production is disruptive, expensive, and fraught with monumental opportunities to screw up." Apple Inc. v.
Dec 21, 2016


Defensive Code Review: Fight Fire With Fire
The pendulum against covered business methods and software continues to swing backward or forward depending on whom you ask. Patent...
Oct 21, 2016
bottom of page
